 According to the report published by Techcare.com, on an average each victim whose website is hacked suffers a loss of 1600 USD. This is an avoidable loss with upcoming technologies such as cloud computing. With cloud security services you can secure your data and share it with stakeholders over a secure network.
According to the report published by Techcare.com, on an average each victim whose website is hacked suffers a loss of 1600 USD. This is an avoidable loss with upcoming technologies such as cloud computing. With cloud security services you can secure your data and share it with stakeholders over a secure network.
Steps to ensure Cloud Security
Make sure you partner with reliable cloud security service providers to secure your information. You should also make sure you have all the possible information on such services to be able to optimize on the benefits this technology is capable of.
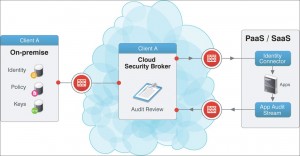
Ask for privileged access: This is implemented by cloud security vendors so that data migration and transfers could be performed securely and smoothly. A good vendor would have enabled such rights but with a filter such that legit users would have similar access to data but would not be allowed to modify it. Encryption allows for higher data security and so only privileged users can access it.
Pre-Determine Responsibility and Accountability: One should implement the up keep of a log that records all access to data. This detail will help account for any mishap that may occur on part of the users. Also the provider should be able to protect the cloud itself from security threats and should be accountable to any mishap/ loss that may occur due to a malfunctioning or hacked cloud. However, given the security levels of the technology there is a bare minimum chance of this happening.
Gain Information of Local laws and Jurisdiction: Whenever cloud storage is done on a remote location, the vendor should ensure that he follows all the laws. There are different regulations that bind such deployment and data security as a whole. Clouds ensure an up keep of regulatory compliance.
Ask about Segregation: Data which is stored on a cloud is like a pool of information. Thus there may be chances of a data mix up in cloud; therefore it is advised that users ask for segmentation and segregation policies used by vendors. They can also chart out the kind of segmentation they want for their data along with the vendors themselves.
Look for Data Recovery options: A good vendor would be able to provide for data recovery in case of any kind of cloud failure. Before inking the final agreement, do highlight your concern about the same. Also check with the vendors about the security of data which is copied for backup.
Before you deploy these services, analyze your individual needs and deploy the features and applications customized to the security issues you face.
To ensure complete cloud security, visit CloudAccess.com. They are a reputed cloud computing and security service provider with secure and affordable services.



